Pod Security in Kubernetes —
Pod security in Kubernetes gives developers and operators enormous flexibility, but that flexibility can also introduce serious security risk if Pods are allowed to run with excessive privileges or unsafe settings. Pod security is about defining and enforcing what Pods are allowed to do — whether they can run as root, mount the host filesystem, use privileged capabilities, access the host network, and so on. This guide explains the modern, supported ways to enforce Pod security in Kubernetes, practical examples, and best practices you can apply today.
Why Pod security in kubernetes matters
A Pod with unrestricted permissions can:
-
Break out of container isolation and access host resources,
-
Read or modify secrets it shouldn’t see,
-
Escalate privileges and move laterally across your cluster.
Most production clusters should minimize privileges and enforce clear guardrails so that developer workloads can’t accidentally (or maliciously) cause cluster-wide harm. Industry benchmarks like the CIS Kubernetes Benchmark explicitly recommend an active policy mechanism to control pod admission and reduce risk.
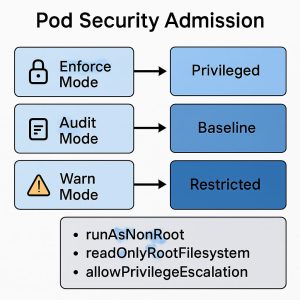
PSP → Pod Security Standards & Pod Security Admission
pod security in Kubernetes originally offered Pod SecurityPolicy (PSP) as a built-in admission controller to limit pod capabilities. PSP was formally deprecated in v1.21 and removed in v1.25. The Kubernetes project replaced PSP with a simpler model based on the Pod Security Standards, enforced by the Pod Security Admission (PSA) controller (GA in v1.25). If you’re still using PSP, plan to migrate.
Pod Security Standards — the safe defaults
The Pod Security Standards (PSS) in kubernetes define three policy profiles that cover a broad spectrum of risk vs. compatibility:
-
Privileged — least restrictive; allows host network, host PID/IPC, privileged containers, etc. (not recommended for general workloads).
-
Baseline — sensible defaults that block known risky fields while allowing most common applications to run (a practical middle ground).
-
Restricted — the most secure profile; denies host access, privileged mode, escalation, and more — best for high-security namespaces.
These standards are intentionally cumulative: restricted is a strict superset of baseline checks. Use the profile that fits the trust level of each namespace.
Enforcing Pod Security: Pod Security Admission (PSA)
The simplest way to enforce Pod Security Standards in a cluster is to use the Pod Security Admission controller. PSA inspects Pods at admission time and either warns, enforces, or audits them based on namespace labels.
Common workflow:
-
Label namespaces with the policy and mode you want (enforce, audit, warn).
-
PSA applies the selected profile checks when Pods are created or updated.
-
Violating Pods are either rejected (enforce), allowed but logged (audit), or allowed with a console/browser warning (warn).
Example: enforce the restricted profile on namespace prod:
This will reject Pod manifests that fail the restricted checks. (See Kubernetes docs for options and behavior.)
How to migrate from PSP to PSA (high level)
If you previously relied on PSP, migration generally involves:
-
Inventory — find Pods that would be rejected by strict policies (use
warnmode to see violations). -
Iterate — run namespaces in
auditorwarnto collect violations and update workloads. -
Adjust — refactor containers to avoid requiring forbidden options (drop
privileged, avoid hostPath where possible, run as non-root, remove hostNetwork unless necessary). -
Enforce — switch namespaces to
enforcewhen confident.
Third-party policy engines like OPA Gatekeeper or Kyverno can help during migration by providing richer policy languages and remediation hooks — but PSA is simple and builtin for many use-cases.
Practical Pod-level controls you should enforce
When designing your Pod security posture, consider banning or constraining:
-
Privileged containers (
securityContext.privileged: true) -
AllowPrivilegeEscalation — should be false unless you really need it
-
Running as root — prefer
runAsNonRoot: trueand setrunAsUser/runAsGroup -
Host namespaces — avoid
hostNetwork,hostPID,hostIPCunless required -
hostPath mounts — restrict or eliminate; prefer CSI volumes or PVCs
-
Capabilities — drop all (
capabilities.drop: ["ALL"]) and add only required ones -
SELinux / Seccomp — enforce runtime confinement profiles (e.g., seccomp
RuntimeDefault) -
ReadOnlyRootFilesystem — enable where possible to limit writeable attack surface
These fields map directly to the Pod Security Standards checks and are commonly enforced by CIS-style checklists.
Example:
Run as non-root and drop capabilities:
Use a stricter seccomp profile (where supported):
Namespaces, RBAC, and defense-in-depth
Pod security in kubernetes is only one layer. Combine PSA with:
-
RBAC to limit who can create/modify Pods or change labels.
-
Network Policies to restrict Pod-to-Pod and Pod-to-service communication.
-
Admission controllers (e.g., image policy webhook) to validate images.
-
Runtime scanning & EDR to detect post-deployment compromise.
CIS and cloud provider guidance also recommend deploying at least one active policy mechanism (PSA, OPA, or cloud policy) as a baseline.
Testing and validation
-
Use
kubectlandpsalabels inwarnorauditmodes to gather violations before enforcing. -
Run conformance/scanning tools (CIS Benchmarks, kube-bench, or built-in cloud policy controllers) to check cluster posture.
-
Include pod-security checks in CI/CD: lint manifests, run policy tests, and prevent merges that would create pods violating the intended profile.
Cloud providers (GKE, EKS, AKS) and managed platforms often provide guidance or builtin policy controllers to make this easier — check your provider docs for specifics.
Common pitfalls & recommendations
-
Too-strict too-fast: Enforcing
restrictedcluster-wide without prior auditing will break many workloads. Start withaudit/warn. -
Relying on security through obscurity: Labels and admission settings need RBAC guardrails — otherwise developers can relabel namespaces to weaken controls.
-
Ignoring runtime defenses: Preventing risky Pods is essential, but runtime monitoring is equally necessary to catch unusual behavior.
-
Thinking PSA covers everything: PSA is great for Pod-level fields, but it doesn’t replace policy engines for complex constraints (e.g., allowed registries, image signing).
Final checklist to secure Pods (quick)
-
Define a cluster-wide baseline (use PSA
baseline) and stricter policies for sensitive namespaces. -
Run
warn/auditscan of namespaces to find violations. -
Update workloads to use non-root users, drop capabilities, set readOnlyRootFilesystem.
-
Enforce via PSA labels or a policy engine (Kyverno / OPA) where you need richer controls.
-
Integrate checks into CI/CD and use CIS benchmarks for periodic aud
Learn more in the [official Kubernetes Pod Security Standards] click here